Securing WiFi networks is paramount due to the escalating prevalence of cyber threats and the associated risks of WiFi hacking. With the rapid digitization, WiFi has become a common target for cybercriminals. Unauthorized access can lead to data breaches and identity theft. As threats evolve, securing WiFi is crucial not just for personal privacy but to safeguard sensitive information and financial data. Implementing robust security measures like encryption and strong passwords is essential to thwart hacking attempts and counter cyber threats. The importance of securing WiFi networks cannot be overstated, influencing the overall cybersecurity posture of individuals and organizations. If you’re looking for how to hack WiFi password, let’s find out the possible ways.
Types of WiFi Encryption and Risks
WiFi encryption protocols are crucial for securing wireless networks and preventing unauthorized access. This overview explores the common encryption standards, their evolution, and the vulnerabilities associated with each.
1. Wired Equivalent Privacy (WEP)
- Introduction to WEP: Once a standard choice, WEP provided basic encryption.
- Vulnerabilities: We can easily crack due to weak key management, making it obsolete.
2. WiFi Protected Access (WPA)
- Evolution to WPA: Improved security over WEP, addressing some vulnerabilities.
- Vulnerabilities: Apply the brute-force attacks; pre-shared keys can be compromised.
3. WiFi Protected Access 2 (WPA2)
- Enhancements in WPA2: Introduced stronger encryption protocols like AES.
- Vulnerabilities: Vulnerable to KRACK attack; WPA2 security relies on a secure passphrase.
Understanding the strengths and weaknesses of WiFi encryption protocols is crucial for effective network security. While newer protocols like WPA3 offer enhanced protection, the choice of encryption should align with the network’s specific needs and considerations. Regularly updating passwords and staying informed about emerging security standards is fundamental to maintaining a secure WiFi environment.
Password Weaknesses
A weak WiFi password acts as an open invitation to potential hackers, exposing your network to various security threats. This blog explores the vulnerabilities associated with weak passwords and the risks they pose.

1. Brute Force Attacks
- Definition: Attackers systematically try all possible passwords until the correct one is found.
- Impact: Weak passwords can be cracked relatively quickly, granting unauthorized access.
2. Dictionary Attacks
- Definition: Attackers use precompiled lists of commonly used passwords.
- Impact: Weak passwords that align with common dictionary entries are susceptible to quick compromise.
3. Credential Stuffing
- Definition: Attackers use username-password pairs obtained from other breaches.
- Impact: Reusing weak passwords increases the likelihood of successful credential stuffing attacks.
4. Rainbow Table Attacks
- Definition: Attackers use precomputed tables to crack hashed passwords.
- Impact: Weak passwords can be rapidly matched against precomputed hashes, compromising security.
5. Social Engineering
- Definition: Attackers manipulate individuals into revealing passwords.
- Impact: Weak passwords are more susceptible to social engineering tactics, such as phishing.
6. WiFi Sniffing
- Definition: Attackers capture and analyze WiFi network traffic to uncover passwords.
- Impact: Weak passwords make it easier for attackers to decipher captured data.
Brute Force Attacks in WiFi: How to Hack WiFi Password
WiFi networks are susceptible to brute force attacks, where hackers employ relentless force to crack passwords and gain unauthorized access. This blog delves into the tools and techniques hackers utilize in these malicious endeavors.
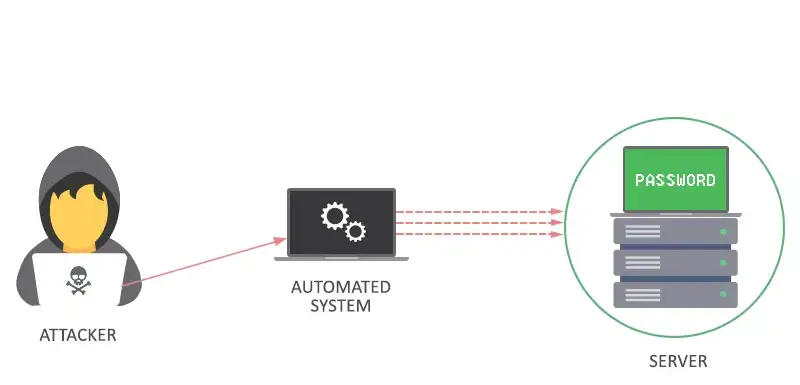
1. Understanding Brute Force Attacks
- Definition: Brute force attacks systematically try all possible combinations until the correct password is discovered.
- Objective: Gain unauthorized access to a WiFi network.
2. Common Tools Used
a. Aircrack-ng
- Overview: A versatile suite of tools for assessing WiFi network security.
- Function: Performs dictionary attacks, capturing WiFi traffic and attempting to crack WPA/WPA2 passwords.
b. Hydra
- Overview: A fast and flexible login password cracking tool.
- Function: Supports multiple protocols, including HTTP, FTP, and routers, making it a choice for WiFi password attacks.
c. Hashcat
- Overview: Advanced password recovery tool supporting various algorithms.
- Function: Capable of attacking WPA/WPA2 hashes using brute force or dictionary attacks.
3. Techniques Employed
a. Dictionary Attacks
- Description: Uses precompiled lists of commonly used passwords.
- Effectiveness: Targets weak passwords often present in dictionaries, increasing the likelihood of success.
b. Mask Attacks
- Description: Specifies a password’s structure, reducing the search space.
- Effectiveness: Speeds up the attack by focusing on likely password formats.
c. Hybrid Attacks
- Description: Combines dictionary and brute force methods.
- Effectiveness: Maximizes the chances of success by covering a broad range of possibilities.
4. Protecting Against Brute Force Attacks
- Use Strong Passwords: Employ complex, unique combinations resistant to brute force attempts.
- Implement Account Lockouts: Temporarily lock an account after multiple failed login attempts.
- Enable Two-Factor Authentication (2FA): Adds an additional layer of security beyond passwords.
Default Router Credentials
Default router credentials pose a significant security risk to WiFi networks. This blog explores the dangers associated with unchanged default settings and emphasizes the importance of securing these entry points.
1. The Default Password Menace
- Default Settings: Manufacturers often ship routers with generic usernames and passwords.
- Widespread Ignorance: Users often overlook changing default credentials, leaving networks vulnerable.
2. Consequences of Unchanged Defaults
a. Unauthorized Access
- Exploitation: Hackers exploit default credentials to gain unauthorized entry into WiFi networks.
- Risk Magnitude: Potential data breaches, unauthorized usage, and network manipulation.
b. Malware Injection
- Targeting Routers: Default credentials make routers susceptible to malware injections.
- Network-wide Impact: Malicious software can compromise all connected devices.
3. Common Default Credentials
a. Admin/Admin
- Widely Used: Many routers come with the default “admin” username and password.
- Risky Prevalence: Users often neglect changing this common default.
b. Username: Admin / Password: 1234
- Ease of Guessing: Hackers exploit predictable combinations for quick access.
- Manufacturer Defaults: Some routers consistently use this combination.
WPS Vulnerabilities
WiFi Protected Setup (WPS) was designed for easy and secure network connections. However, this blog delves into the vulnerabilities associated with WPS and how attackers can exploit them.
1. Understanding WPS
- Simplified Setup: WPS was created to simplify the process of connecting devices to WiFi networks.
- Methods: WPS allows users to connect by entering a PIN, pressing a button, or using Near Field Communication (NFC).
2. Common WPS Vulnerabilities
a. PIN Vulnerability
- Brute Force Attacks: Attackers can use brute force methods to guess the eight-digit PIN.
- Weakness in Design: The limited number of possible combinations makes PINs susceptible.
b. Weak Authentication
- Default PINs: Some routers use default PINs that are publicly available.
- Predictable Patterns: Attackers exploit routers using predictable algorithms for PIN generation.
3. Potential Exploits
a. Reaver Attack
- Brute Force Technique: Reaver is a tool that exploits WPS by repeatedly attempting PINs.
- Vulnerability: It takes advantage of the weakness in the time delay between PIN attempts.
b. Pixie Dust Attack
- Weakness in Key Exchange: Pixie Dust focuses on vulnerabilities in the key exchange process.
- Decrypting Keys: Attackers can decrypt the WPS PIN and gain access to the WiFi network.
Rogue Access Points of WiFi
Rogue access points are unauthorized and potentially malicious WiFi access points that are set up without the knowledge or consent of the network administrator. These rogue devices can compromise WiFi security by creating an entry point for attackers to infiltrate a network. The threat arises when unsuspecting users connect to these rogue access points, unknowingly exposing their devices and sensitive information to potential attacks.
Attackers may use tactics like man-in-the-middle attacks or injecting malicious payloads. To reduce this risk, network administrators should use robust security measures like regular monitoring, intrusion detection, and strong authentication. Educating users about the dangers of connecting to unknown networks is crucial in preventing WiFi security compromise by rogue access points.
Evil Twin Attacks on WiFi
Evil twin attacks involve the creation of a malicious duplicate WiFi network that appears to be a legitimate and trusted network. Attackers set up a rogue wireless access point with the same or a similar name as a legitimate network, tricking users into connecting to it. This malicious twin may have a stronger signal or a more accessible location, making it an attractive option for unsuspecting users.
Once connected, attackers can intercept and monitor the data transmitted between the user and the network, leading to potential data theft or other malicious activities.
To execute evil twin attacks, hackers utilize tools that allow them to clone the configuration settings of a legitimate WiFi network. This enables them to replicate the network’s SSID (Service Set Identifier) and security protocols, making the malicious twin virtually indistinguishable from the authentic network.
Users often fall victim to these attacks due to the difficulty of discerning between the genuine and malicious networks, emphasizing the importance of vigilance and security awareness to mitigate the risks associated with evil twin attacks. Employing strong encryption, regularly updating passwords, and using technologies like WPA3 can add layers of protection against such WiFi security threats.
Man-in-the-Middle (MitM) Attacks
In WiFi, a Man-in-the-Middle (MitM) attack occurs when a malicious actor intercepts and potentially alters communication between two parties without their knowledge, compromising sensitive information. Common WiFi MitM Techniques include Packet Sniffing, ARP Spoofing, DNS Spoofing, SSL Stripping, and Rogue Access Points.
MitM attacks underscore WiFi network vulnerability, emphasizing the importance of robust encryption, secure protocols like WPA3, and vigilance against suspicious activity to mitigate risks associated with unauthorized access and interception
Packet Sniffing
Packet sniffing, a technique central to WiFi hacking, involves intercepting and analyzing data packets transmitted over a network. In WiFi, this method allows attackers to gain insights into the information exchanged between devices and the network.
Role of Packet Sniffing in WiFi Hacking
- Data Interception: Attackers capture packets to access sensitive data, such as login credentials, personal information, or financial details.
- Network Mapping: Packet sniffing aids in understanding the structure and flow of a WiFi network, enabling attackers to identify potential vulnerabilities.
- Traffic Analysis: Analyzing packet headers and content helps hackers discern patterns, usage behaviors, and potential weaknesses in the network’s security.
Tools Used for Packet Sniffing in WiFi Hacking
- Wireshark: A widely-used open-source packet analyzer, providing detailed insights into network traffic.
- Tcpdump: A command-line packet sniffer capable of capturing and displaying packet data on the terminal.
- Cain and Abel: A versatile hacking tool that includes packet sniffing capabilities for WiFi networks.
- Ettercap: A comprehensive suite for Man-in-the-Middle (MitM) attacks, including packet sniffing functionalities.
Understanding packet sniffing is crucial for both ethical hackers and network administrators to bolster defenses against potential threats. Implementing encryption protocols like WPA3 and maintaining secure network practices can mitigate the risks associated with packet sniffing in WiFi environments.
DNS Spoofing
DNS spoofing, or DNS cache poisoning, is a malicious technique where attackers provide false DNS responses to redirect users to fraudulent websites. In the context of WiFi security, DNS spoofing poses significant risks.
Impact on WiFi Security
- Phishing Attacks: Spoofed DNS responses can lead users to malicious websites, facilitating phishing attempts to steal sensitive information.
- Man-in-the-Middle (MitM) Attacks: Attackers can intercept and alter DNS queries, enabling them to eavesdrop on communication between devices and the internet.
- Traffic Hijacking: DNS spoofing allows attackers to reroute network traffic through malicious servers, giving them control over data transmission.
Countermeasures to Prevent DNS Spoofing
- DNS Security Extensions (DNSSEC): Implementing DNSSEC adds cryptographic signatures to DNS data, ensuring the integrity and authenticity of DNS responses.
- Use of DNS Filtering: Employ DNS filtering services to block access to known malicious domains and prevent users from connecting to potentially harmful sites.
- Regular Software Updates: Keep DNS software and systems up-to-date to patch vulnerabilities and reduce the risk of exploitation.
- Network Segmentation: Segmenting networks limits the impact of DNS spoofing by containing the attack within specific network segments.
- Intrusion Detection Systems (IDS): Deploy IDS to monitor and detect unusual DNS traffic patterns, triggering alerts for potential spoofing attempts.
Understanding the mechanics of DNS spoofing and adopting these countermeasures is crucial for safeguarding WiFi networks against this pervasive threat, preserving the integrity of data transmission and ensuring a secure online experience for users.
Firmware Exploits on WiFi
WiFi router firmware, the embedded software controlling the router’s functionality, is a critical component of network security. However, exploiting vulnerabilities in router firmware can have severe consequences.
Exploited router firmware vulnerabilities pose multiple risks
- Unauthorized Access: Attackers exploit vulnerabilities, compromising router settings and gaining unauthorized network access.
- Malicious Firmware Installation: Intruders inject malicious firmware, gaining persistent control and exposing the network to cyber threats.
- Denial-of-Service (DoS) Attacks: Vulnerabilities enable DoS attacks, disrupting services and causing connectivity issues.
- Privacy Breaches: Attackers intercept and manipulate data, leading to privacy breaches and theft.
Preventing Exploitation of Router Firmware Vulnerabilities
- Regular Firmware Updates: Routinely update router firmware to patch known vulnerabilities and strengthen security measures.
- Strong Authentication: Implement robust password policies and use strong, unique passwords for router access to prevent unauthorized entry.
- Vendor Security Advisories: Stay informed about security advisories from router manufacturers to address newly discovered vulnerabilities promptly.
- Network Segmentation: Segment networks to minimize the impact of a compromised router, containing potential threats within specific network segments.
- Network Monitoring: Employ network monitoring tools to detect unusual or suspicious activities, enabling quick responses to potential firmware exploitation attempts.
Understanding the risks associated with WiFi router firmware vulnerabilities and taking proactive measures to address and mitigate these vulnerabilities are crucial steps in maintaining a secure and resilient wireless network.
Continuous awareness, prompt updates, and proactive security measures are key to safeguarding your WiFi network against evolving threats. Stay informed, adopt the latest security practices, and ensure your WiFi remains a fortress in the digital realm.